LDAP Configuration
Deepser natively supports integration with the LDAP protocol.
LDAP is a protocol for centralized resource management.
Deepser’s LDAP integration allows you to easily import users and or groups containing users that you will need to be enrolled to be managed/enabled in Deepser from an existing LDAP installation.
Note that Deepser synchronizes resources with LDAP in read-only mode and can independently manage the update of states or generally modified parameters on the LDAP Resources placed in the LDAP controller, this translates into the fact that if a user is moved to group or disabled or in general changes are made to the user on the LDAP controller the same changes, in a standard case, will be replicated on Deepser.
CONFIGURING LDAP INTEGRATION
To configure an LDAP integration on Deepser you will need to go to the System -> Permission -> LDAP Integration menu
In the screen that will open, you will be able to view the LDAP integrations already configured and configure new ones.
To configure a new integration, you will need to click on the Add LDAP button.
After that the following screen will open:
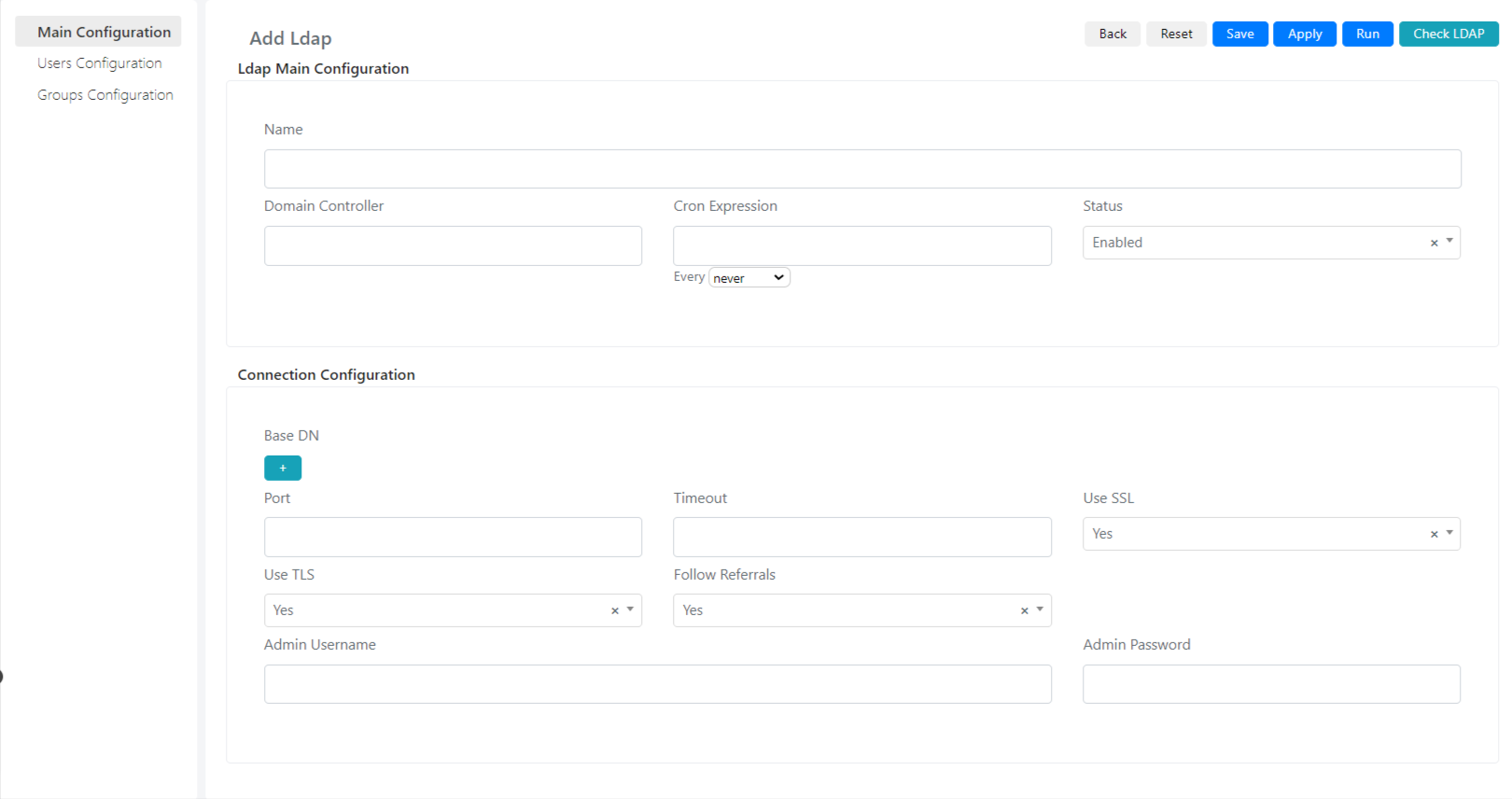
Below are the fields present and their meaning:
| Field | Description |
| Show In Login | This field indicates whether this LDAP integration will be visible on the login page |
| Is Default | Indicates whether this LDAP integration will be the one selected by default in the list on the login page |
| Name | LDAP Integration Name |
| Domain Controller | The address at which to find the domain controller. |
| Cron Expression | Cron expression that indicates how often the integration will be performed. |
| Status | Indicates whether this integration is active or not, if it is not active the synchronization will not be performed. |
| Base DN | Domain base name, this field indicates the point below which Deepser will have visibility in the domain forest. |
| Time-out | Indicates the maximum time within which if a request is not answered, the request must be considered expired. |
| Use SSL | Indicates whether the domain controller uses S.S.L. encryption |
| Use TLS | Indicates whether the domain controller uses T.L.S. encryption |
| Follow Referrals | This field indicates whether to follow the referral links generated by the LDAP controller. Referral links are links that indicate that the server you are querying does not directly own the requested resource, but has a reference to the server or domain that owns that resource. |
| Admin Username | Username of the user that Deepser will use to read domain’s users. |
| Admin Password | Password of the user account that Deepser will use to read access the Domain Controller. |
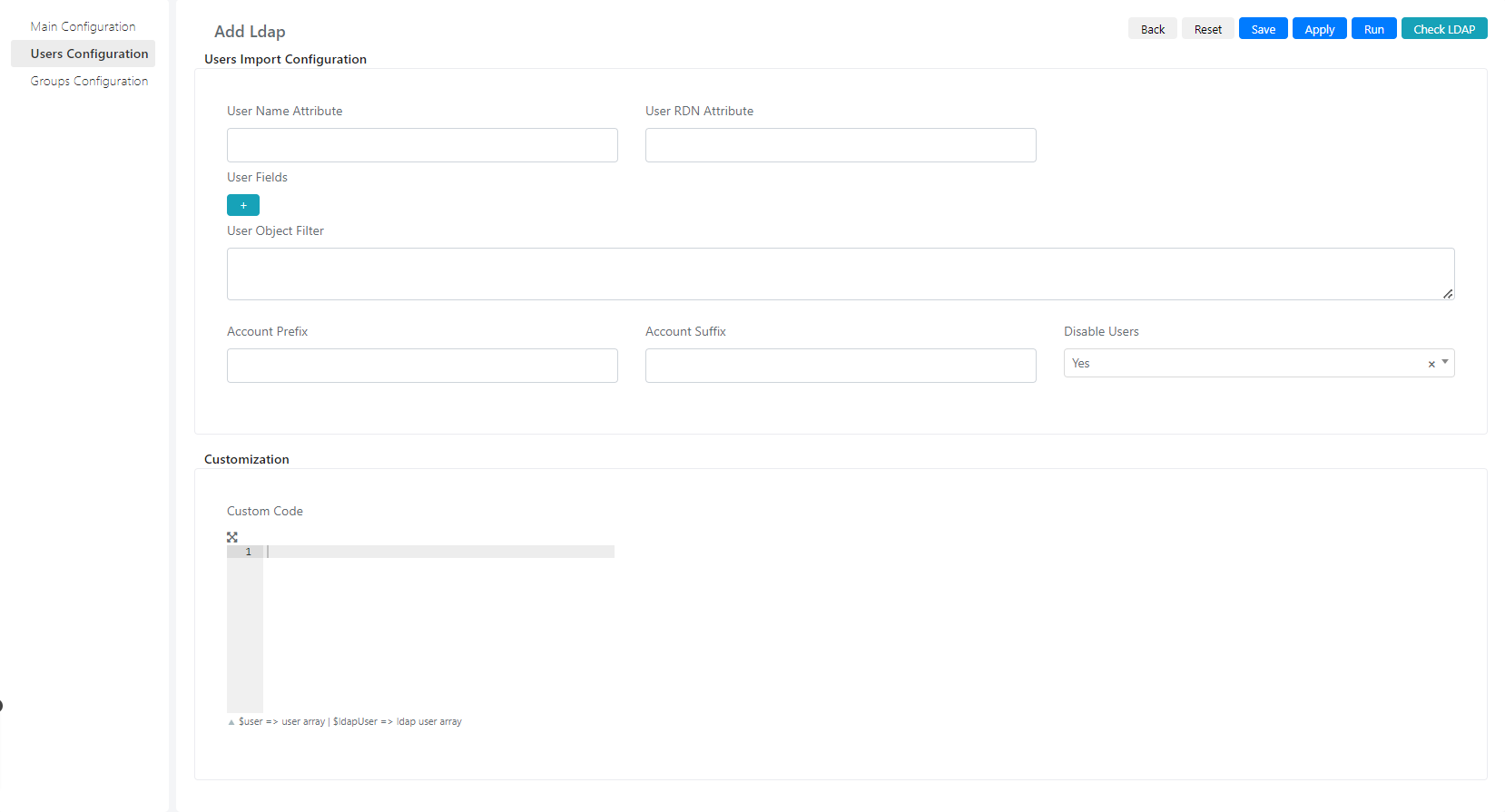
In the Users Configuration section, you will define how users will be synchronized in Deepser.
Below are the fields in this section and their meaning:
| Field | Description |
| User Name Attribute | Indicates which field of the response obtained from the domain controller will contain the user’s name |
| User RDN Attribute | This field is the field that indicates the path relative to another entity (parent) of the resource in the Domains Forest . ES: distinguishedname. |
| User Fields | This field is used to map the relation between domain user’s fields and user’s fields in Deepser |
| User Object Filter | This field is used to specify an LDAP query, this will serve as a filter to retrieve only users who match the search criteria. |
| Account Prefix | Account prefix e.g.: “EXAMPLE\<username>”. In this case “EXAMPLE\” is the account prefix. |
| Account Suffix | Account suffix ex: “<username>@example.local”. in this case “@example.local” is the account suffix. |
| Disable Users | This field indicates whether users created on AD as disabled should be imported as disabled or not. |
| Custom Code | Custom code to indicate how user field values imported from integration are assigned. |
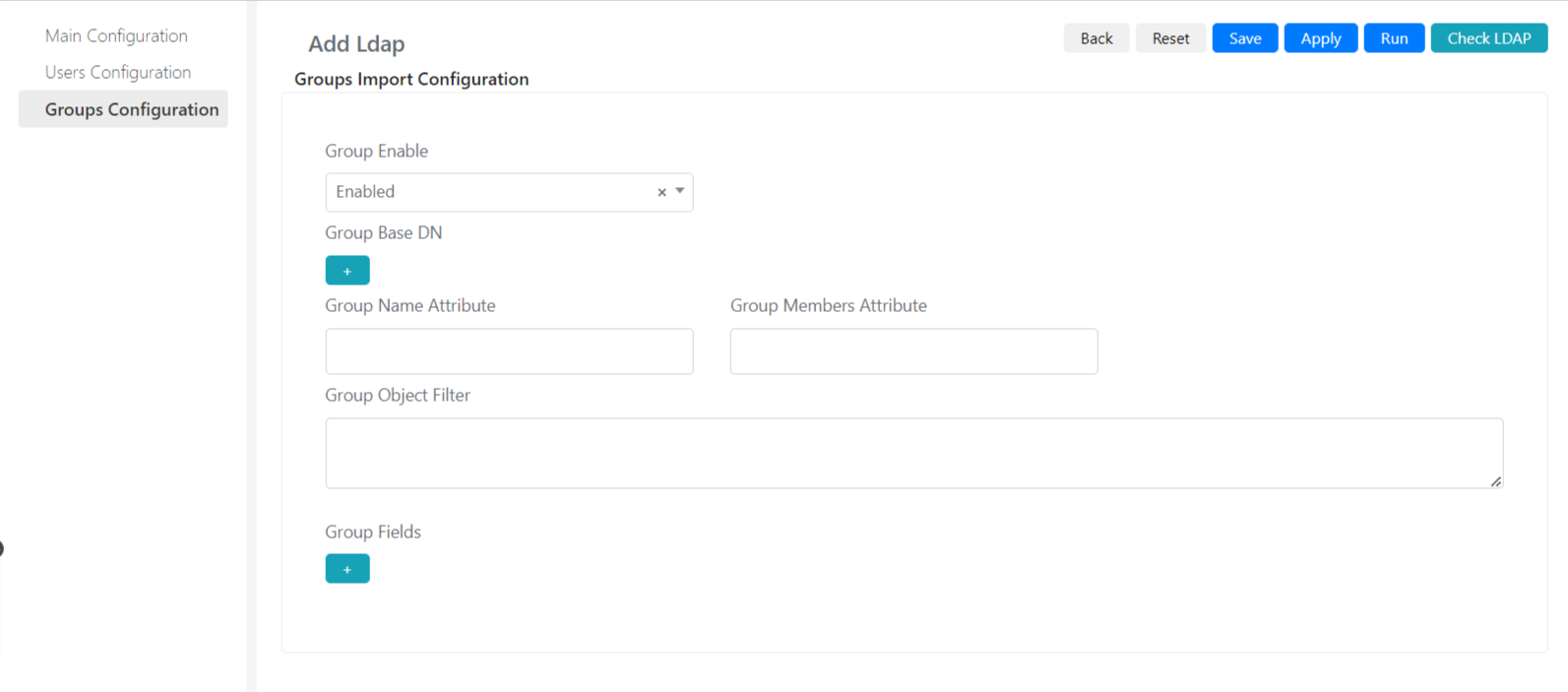
In the Groups Configuration section, you will define how groups will be synchronized in Deepser.
Below is a list of the fields present and their meaning:
| Field | Description |
| Group Enable | This field is used to enable the import of groups into Deepser from the forest. |
| Group Base DN | Indicates which is the name of the base domain in which the groups reside (e.i.: cn=exemple, dn=com) |
| Group Name Attribute | Indicates which field in the object returned by the request to the domain controller will contain the name of the group. |
| Group Members Attribute | Indicates which field in the object returned by the request to the domain controller will contain the list of users who belong to the group |
| Group Object Filter | This field is used to specify an LDAP query, this will serve as a filter to retrieve only the groups that match the search criteria. |
| Group Fields | This field is used to bind domain group fields to group fields in Deepser |
Once the fields have been configured, you will need to click on the “Save” or “Apply” button.
At this point, by clicking on the “Check LDAP” button, you can check if the integration works correctly.
If the integration works correctly, a green banner will be displayed in the upper right corner of the page.
In case of error, you will see a red banner in the upper right corner of the page.