OAuth Client for Email Integration
Some systems require web applications, such as Deepser, to perform authorization before they can use their services.
Deepser allows you to configure multiple OAuth clients in order to authorize it , through the OAuth2 protocol, on different services.
CONFIGURATION
To configure an OAuth client in Deepser, navigate to the System-> Tools->OAuth->Client section.
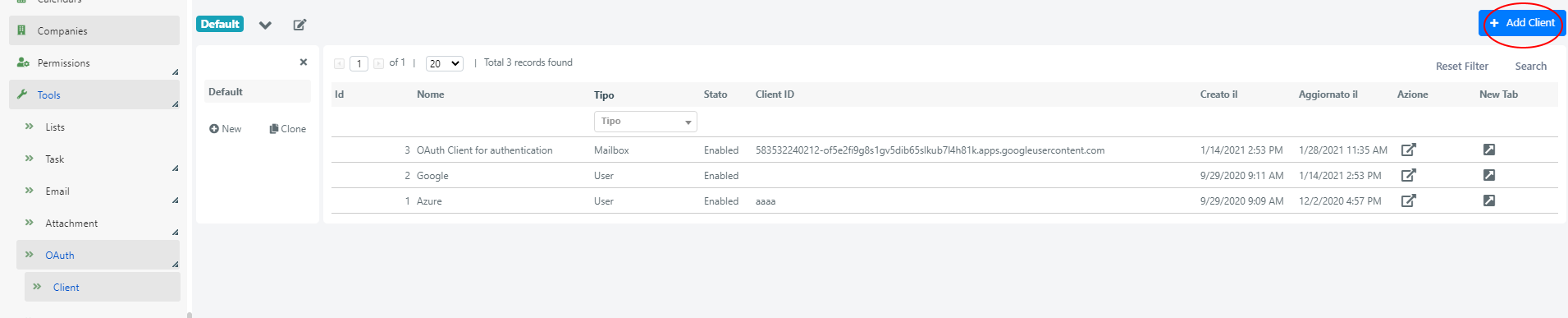
You will see a grid containing all oauth clients defined as Deepser.
To configure a new client click on the ‘+ Add Client’ button in the top right corner.
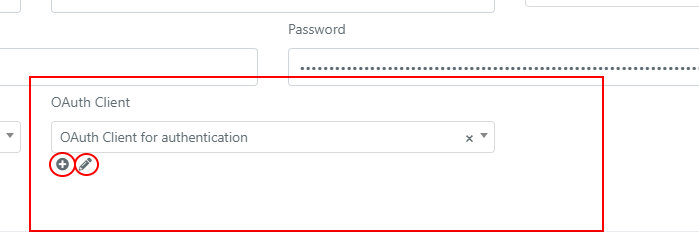
A new OAuth Client can be also created and configured from the configuration form of a mailbox.
Under the OAuth Client field, of the Select type, whose options are the already configured clients, clicking on the ‘+’ icon allows you to create a new client, while clicking on the ‘pencil‘ icon allows you to modify the configuration of the selected client.
The fields of the configuration form of an OAuth client are listed and explained below:
| FIELD | MEANING |
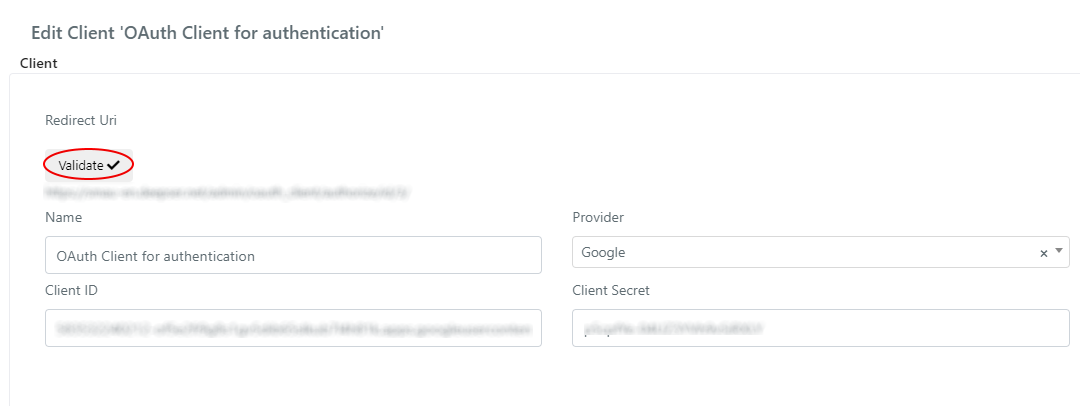
| Redirect Uri | Deepser Url from which Deepser which will send requests to the provider. The URL must be authorized in the administration panel of provider. The URL will appear once the client is saved. After saving, the ‘Validate‘ button will appear, by ckicking it you can authorize the client once its configuration is complete. |
| Name | Client name. It represents a descriptive field with which the client will be displayed in the system. |
| Provider | Provider: Google, Azure, Generic. If you use Google or Azure as a provider the only other fields that must be filled are Client ID, Client Secret and status. Generic value is used to configure the authentication to all other providers. |
| Client ID | Public identifier for applications. It is provided by the provider, usually when a new application is authorized. |
| Client Secret | Secret part of the authentication credentials. It is provided by the provider. |
| Type | Type of data you want to access/recover. |
| Scope | Scopes to which the application requires access. No need to fill it for Google or Azure providers, default values will be used. |
| Url Authorize | It is the ‘base URL’ of the Identity Provider that manages OAuth 2 authentication. No need to fill it for Google or Azure providers, default values will be used. |
| Url Access Token | This is the ‘base URL’ to which the parameters for requesting the authentication token are added (post-authorization step). No need to fill it for Google or Azure providers, default values will be used. |
| Proxy | IP address and port of any used proxy. It is not necessary for Google or Azure providers, default values will be used. |
| Verify | If a proxy has been configured you can enable or disable the SSL check. No need to fill it for Google or Azure providers, default values will be used. |
| Status | If ‘disabled’ the client is not active. |
| Scope Separator Char | Character used to separate different scopes. Used during the construction of the request url. No need to fill it for Google or Azure providers, default values will be used. |
| Endpoint User Data | In case the OAuth configuration is User type and the User Data Source is set to ‘Endpoint’, once the authentication is done with the Identity Provider the user data is retrieved by connecting to this endpoint. No need to fill it for Google or Azure providers, default values will be used. No need to fill it for Email Box type. |
| Related LDAPs | Any LDAP integrations already configured, whose users must be linked. No need to fill it for Email Box type, the default values will be used. |
| Username Attribute | Attribute (field) that desctibe the user’s username. No need to fill it for Google or Azure providers, default values will be used. No need to fill it for Email Box type. |
| User Fields | Maps the user (Deepser entity) attributes to those retrieved from the specified user data endpoint. No need to fill it for Google or Azure providers, default values will be used. No need to fill it for Email Box type. |
| User Create Expression | PHP code for configuring the user creation, for example in case of an SSO integration. No need to fill it for Email Box type. |
| Login Button Caption | Button label for access via SSO. No need to fill it for Email Box type. |
| Login Button Icon | Icon displayed on the SSO authentication button. No need to fill it for Email Box type. |
| Access Token | This field is not filled out in the form for security reasons. It contains the serialized access token. |
| Original Access Token | This field is not filled out in the form for security reasons. It contains the serialized access token. |
Once the form has been completed and the OAuth client configuration has been re-saved, you can validate it.
Just click on the ‘Validate‘ button that will appear once the client is saved for the first time.
Authenticate on Provider through the form that will appear, once logged in the client is authorized.